Summary:
In the world of cybersecurity, Capture The Flag competitions for hackers have become one of the most effective ways to learn, practice, and validate real security skills. Whether you’re a student entering cybersecurity for the first time, a professional preparing for certifications, or an enthusiast who simply enjoys technical puzzles, CTFs provide a safe, legal, and challenging environment to test your abilities.
Table of Contents
What Are Capture The Flag Competitions for Hackers?
Main Types of Capture The Flag Competitions
Practical Experience Gained From Capture The Flag Competitions
2. Deep Understanding of Tools and Techniques
3. Improved Problem-Solving and Creativity
4. Building a Portfolio and Professional Credibility
5. Collaboration and Team Experience
How to Start Participating in Capture The Flag Competitions for Hackers
Gamification plays a key role in Capture The Flag competitions for Hackers.
In the world of cybersecurity, Capture The Flag competitions for hackers have become one of the most effective ways to learn, practice, and validate real security skills. Whether you’re a student entering cybersecurity for the first time, a professional preparing for certifications, or an enthusiast who simply enjoys technical puzzles, CTFs provide a safe, legal, and challenging environment to test your abilities.
These competitions simulate real-world cyberattacks and defensive scenarios through structured challenges. By participating, hackers and security practitioners get hands-on experience with penetration testing, coding, forensics, networking, and much more—skills that are essential in both offensive and defensive security careers.
This guide breaks down the most common types of Capture The Flag formats, the practical skills you gain, and why every aspiring cybersecurity professional should experience CTFs first-hand.
What Are Capture The Flag Competitions for Hackers?
Capture The Flag (CTF) competitions are cybersecurity challenges designed to test problem-solving, creativity, and technical knowledge. Participants search for “flags,” which may be hidden pieces of text, tokens, or files that can be found only by solving a cybersecurity challenge.
Although the phrase “for hackers” may sound intimidating, it simply refers to ethical and educational hacking. CTFs allow participants to think like hackers—but in a controlled, ethical learning environment.
The popularity of Capture The Flag competitions for hackers continues to rise because they:
- Provide hands-on training that no textbook can replicate
- Simulate real-world cyber incidents
- Improve teamwork and communication
- Enhance job-readiness for cybersecurity careers
- Allow hackers to measure their skills against others globally
Main Types of Capture The Flag Competitions
CTFs vary depending on the skills they test and how the competitions are structured. Understanding the main categories helps participants choose the right style for their goals.
1. Jeopardy-Style CTFs
This is the most common beginner-friendly format. Participants face a board of challenges categorized by topics, each with increasing levels of difficulty.
Typical categories include:
- Cryptography – cracking encryption, analyzing ciphers
- Web Exploitation – identifying vulnerabilities like XSS, SQL injection
- Reverse Engineering – deconstructing binaries to find hidden flags
- Forensics – analyzing logs, memory dumps, or network packets
- OSINT (Open-Source Intelligence) – gathering information from publicly available sources
Jeopardy-style CTFs focus on puzzle solving and technical knowledge rather than attacking live systems. This makes them ideal for new learners.
A typical Jeopardy-style CTF might include a challenge where participants must decrypt a message using a specific cipher. For example, a challenge might provide a string encrypted with the Caesar cipher and require participants to write a script to decrypt it. In Python, this could be done using a simple loop:
for shift in range(26):
decrypted = ''.join(chr((ord(char) - shift - 65) % 26 + 65) if char.isupper() else char for char in encrypted_text)
print(f'Shift {shift}: {decrypted}')This code snippet demonstrates the iterative process of testing each possible shift value until the correct decryption is found. Such exercises hone problem-solving skills and familiarity with programming languages.
2. Attack-Defense CTFs
This format simulates real cybersecurity operations. Each team:
- Defends its own vulnerable system
- Attacks other teams’ systems
- Patches vulnerabilities while attempting to exploit others
Attack-Defense CTFs are fast-paced, highly competitive, and perfect for participants who enjoy offensive and defensive security combined. They require teamwork, communication, and rapid decision-making.
On the other hand, involve teams defending their own servers while attempting to attack others'. This format closely mimics real-world cybersecurity operations.
In Attack-Defense CTFs, participants must secure their systems against intrusions while exploiting vulnerabilities in opponents' systems. This requires a deep understanding of network protocols, system administration, and security tools. Tools like Wireshark for packet analysis or Metasploit for penetration testing are commonly used.
3. King-of-the-Hill CTFs
A dynamic variation of the Attack-Defense CTFs where competitors fight to control a particular machine or resource. Points are awarded based on:
- How long you maintain control
- How well you defend your position
- How effectively you remove attackers
This style emphasizes persistence, strategy, and adaptability—much like real-world network security.
Practical Experience Gained From Capture The Flag Competitions
CTFs are not only about technical skills. They also emphasize teamwork, communication, and strategic thinking. Teams must coordinate their efforts, share knowledge, and adapt to rapidly changing scenarios. This mirrors the collaborative nature of real-world cybersecurity efforts. Here’s what participants truly gain:
1. Real-World Security Skills
Unlike traditional learning, CTFs force you to solve problems that mirror real-world attacks. You learn:
- Identifying vulnerabilities
- Writing exploits
- Using penetration testing tools
- Analyzing malware
- Investigating compromised systems
These hands-on skills translate directly to security analyst, penetration tester, SOC, and forensics roles.
2. Deep Understanding of Tools and Techniques
Capture The Flag competitions for hackers require proficiency with tools such as:
- Burp Suite
- Metasploit
- Wireshark
- Ghidra
- John the Ripper
- Nmap
- Python scripting
Instead of just reading about them, you get direct experience using them under pressure.
3. Improved Problem-Solving and Creativity
Many CTF puzzles require unconventional thinking. Competitors often say that CTFs teach them to:
- Break problems into smaller parts
- Design creative solutions
- Think like an attacker
- Adapt quickly under time constraints
These are crucial traits for cybersecurity professionals.
4. Building a Portfolio and Professional Credibility
CTF participation shows initiative and skill—qualities sought by employers. Competitors can showcase:
- Achievements on scoreboards
- Flags captured
- Write-ups documenting how challenges were solved
This becomes valuable proof of competency during job applications.
5. Collaboration and Team Experience
Attack-Defense and hybrid CTFs require coordinated teamwork. Participants learn:
- Task delegation
- Real-time communication
- Combining complementary skills
This mirrors how modern cybersecurity teams operate.
How to Start Participating in Capture The Flag Competitions for Hackers
If you're new to CTFs, here is a simple roadmap:
- Start with Jeopardy-style platforms to build foundational skills.
- Study basic cyber concepts: web security, Linux commands, cryptography basics, and networking.
- Practice with small challenges daily, even 15–20 minutes.
- Join communities—Discord servers, Reddit groups, and local cybersecurity clubs.
- Move to attack-defense events once you’re comfortable with tools and teamwork.
Consistency is more important than intensity. Treat CTFs like gym workouts for your hacking skills.
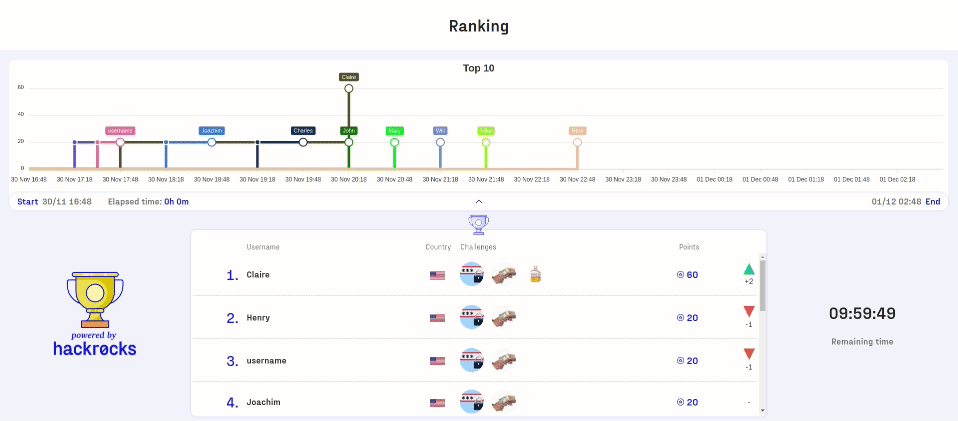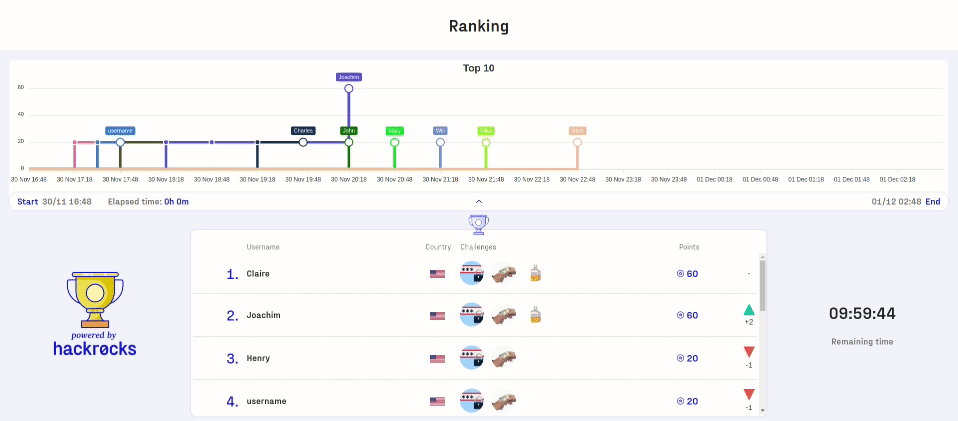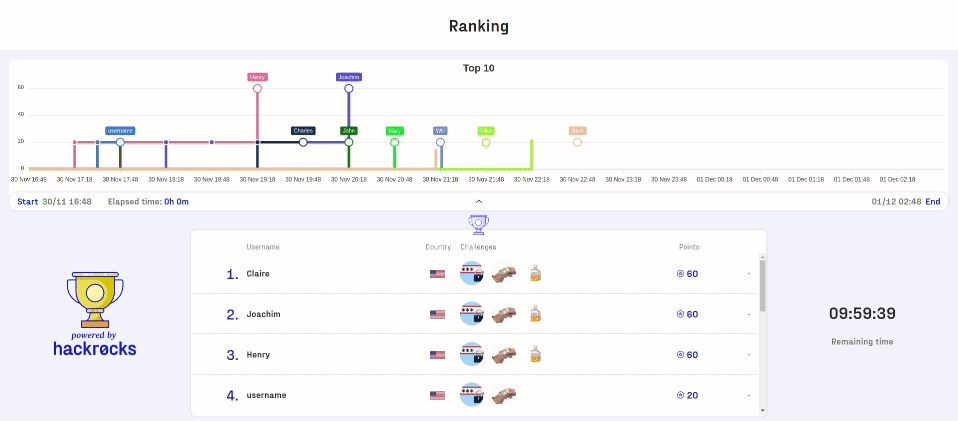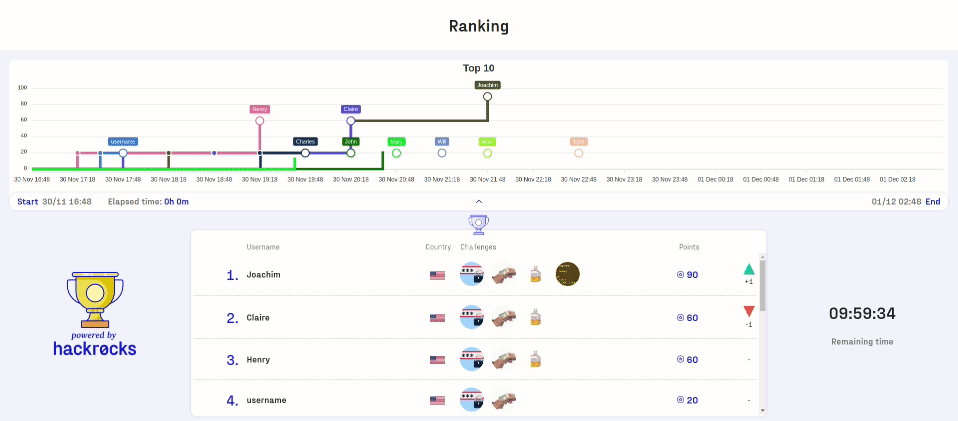
Gamification plays a key role in Capture The Flag competitions for Hackers.
By introducing elements such as points, levels, and rankings, participants experience continuous motivation and a sense of achievement as they progress. Seeing their position on the leaderboard fosters healthy competition and drives teams to push their limits. This dynamic not only makes learning more engaging but also reinforces commitment and collaboration, turning cybersecurity training into a truly immersive experience.
Want to Create Your Own CTF? Here’s a Great Resource
If you’re interested in designing challenges instead of just solving them, hackrocks has an excellent guide:
“Tips and Tactics for Creating Your Own Capture The Flag (CTF)”
It provides practical insights on how to structure challenges, ensure difficulty balance, and design engaging puzzles for learners and professionals alike. If you’ve ever thought about hosting your own event or creating challenges for your community, that article is an outstanding starting point.
At hackrocks, we design customized Capture The Flag experiences for companies of all sizes. From awareness programs for non-technical staff to advanced red team simulations for security professionals, our CTFs are adapted to each organization’s maturity level and objectives. If you want to boost your team’s cybersecurity capabilities and turn learning into an engaging, measurable experience, contact us to discover how a tailored CTF can transform the way your company trains and motivates its people.